Social engineering attacks are on the rise. In fact, they’re among the most successful and insidious types of cybercrime active today.
Worst of all, you can’t protect yourself from all social engineering attacks by just boosting your computer security. A good social engineering attack doesn’t target your software. Instead, it targets the human element. It tries to trick you, often by playing on your emotions.
Social engineering attackers are scammers who use human emotions as the tools of their trade.For example, you could have the world’s most secure video conferencing software, but all that cybersecurity means nothing if a scammer manages to convince the conference host that they deserve an invite.
To protect yourself from social engineering attacks, you need to secure your mindset as well as your technology. Let us show you how.
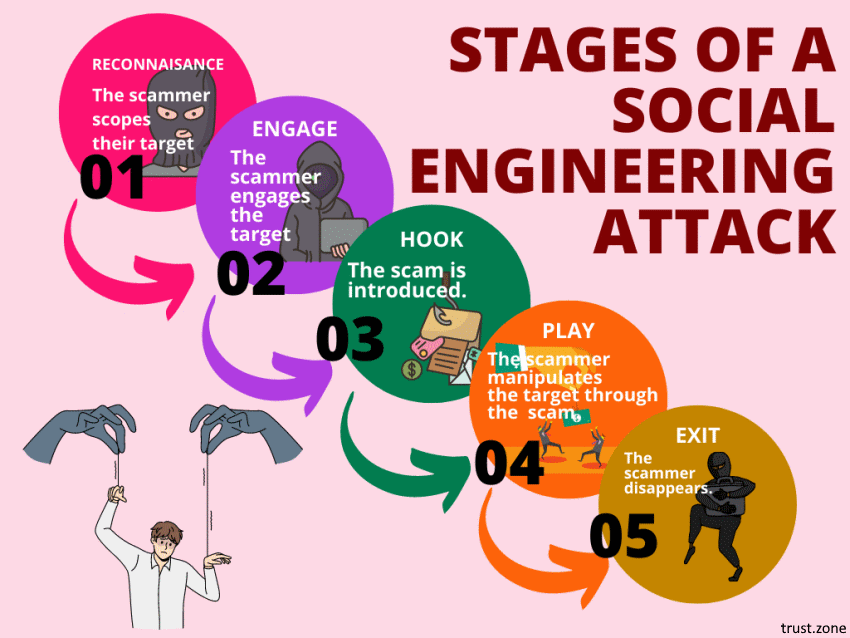
Social engineering attacks aren’t what people think of first when they hear the word ‘cybercrime’. Criminals who use social engineering aren’t masked geniuses in darkened rooms, coding their way through screens of scrolling green numbers.
Instead, social engineers work by manipulating human nature. They are fraudsters, who try to get us to hand over information, or money, or data.
For example, social media phishing posts (‘Your clown name is the name of your first childhood pet and your mother’s maiden name! Tell us yours in the comments!’) are social engineering attacks. Online romance scams are social engineering attacks. Nigerian Prince scams are social engineering attacks.

There are lots of different types of social engineering attacks, but ultimately they all attempt to prey on our emotions and desires. Curiosity, greed, compassion, empathy, fear, love - all of these and more can be manipulated by social engineering scammers.
For example, a common tactic is for scammers to contact you posing as one of your loved ones. They will claim to be in trouble, and to need your help urgently. They will say that they desperately need funds in order to get out of their situation, and ask for you to send them money.
People who fall for this aren’t necessarily stupid or gullible - they are upset by the thought of their loved one being in trouble, and the sense of urgency in the messages prevents them from stopping to think.
Social engineering scams are highly manipulative, and very insidious. The human element makes them hard to combat. After all, you can’t install anti-malware software into your own emotions.
What you can do, however, is learn new ways of thinking and operating on the internet.
Let’s go through some ways that you can protect yourself as a private individual and as a business from social engineering attacks:
Social engineering attacks may be opportunistic, but they usually have a goal in mind. The scammer wants something that you can provide.
So, identify what a scammer may want from you, and operate a low or no trust policy around these assets.
For example, if someone asks you for money, be prepared to think critically about the situation and to fully verify both their identity.
In a business context, don’t make the cybersecurity mistake of not ranking your assets. Instead, carefully consider what assets scammers are most likely to target. Databases, logins, client accounts, intellectual property - all of these and more could look very attractive to a scammer.
Go through your assets, identify the critical ones, and apply an antitrust policy to these assets.
Let’s say, for example, that a company gets in touch and offers to give you a fantastic enterprise process transformation at a low, low price…but first they need access to your databanks. If you’ve already identified databanks as a critical asset, this will set off warning signs.
Because you’re aware that your data may be targeted by scammers, you will be prepared to ask the right questions and proceed with caution.
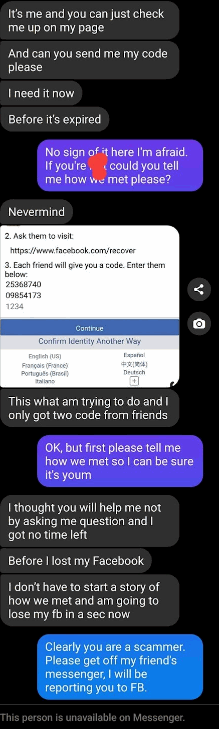 If something appears on your digital radar and you’re not sure exactly where it’s from, don’t trust it blindly.
If something appears on your digital radar and you’re not sure exactly where it’s from, don’t trust it blindly.
For example, if you get an SMS saying that you’re eligible for a tax rebate, check before you click. Look into your tax account to see if a rebate is mentioned. Check the send number. Check the official policy for rebates. If any one of these things doesn’t add up, don’t click that link!
If you’re not sure, go straight to the purported source to confirm (and make sure that you go to that source in a way that doesn’t involve the potential scam itself). For example, if you get a message from someone claiming to be your mother in need of funds, ring your mother and ask if it’s really her.
The most opportunistic scammers will go in ‘cold’, with no or limited information about their targets. They hope that people will be so caught up in their story that they won’t ask tricky questions.
So, if someone messages you claiming to be someone you know, and they want something that seems a bit suspicious, ask them a question that the true person would know but which a scammer or an automated machine learning algorithm would not.
If they can’t answer this question, they will probably try and apply pressure in order to move the scam past this awkward point. Hold firm. A true friend or colleague is unlikely to have a problem with quickly answering an easy question, so if they refuse to answer, make excuses, get angry, ignore the question, or try to escalate past the question, don’t trust them.
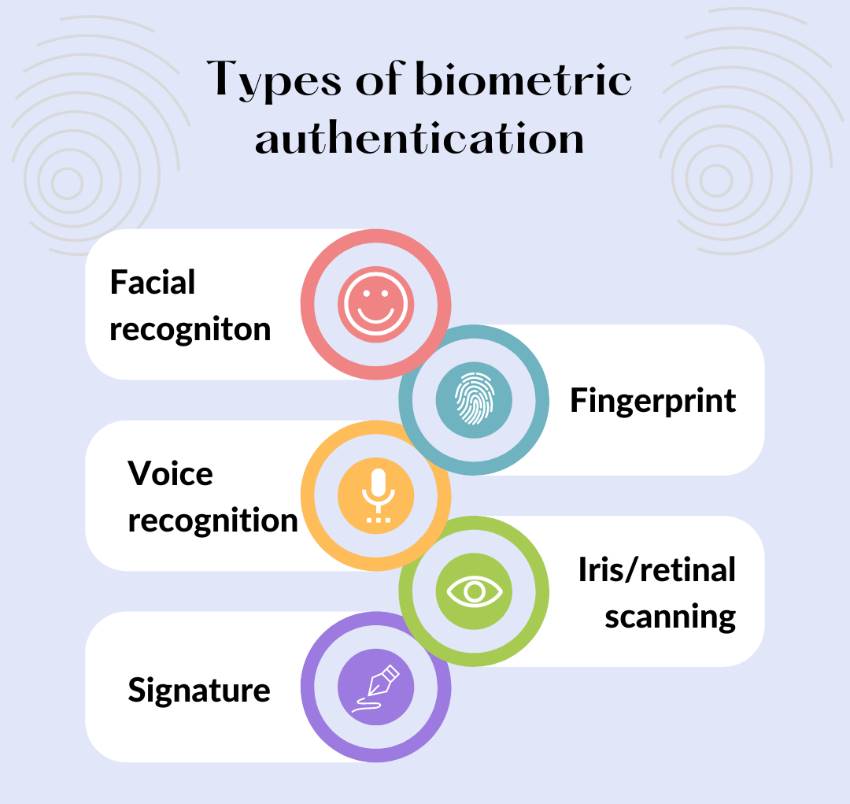
You can add an extra layer of protection to critical accounts with multi-factor authentication. This means that even if an attacker manages to get one password, they will still be unable to access your account.
One of the best ways to do this is to add a biometric element to your authentication. For example, in order to sign into an account you would need both a password (which a scammer could steal and use) and your thumb-print (which they can’t).
This isn’t always possible - not every computer has a fingerprint scanner or facial recognition capabilities, and not all platforms enable biometric factors. But, where you can, it’s well worth doing.
Another option is to use an e-signature to access your account. You can easily use an eSign documents free account, and the security features around your e-signature can make it as effective and unique as the biometric signature.
Quite honestly, if you’re not already using multi-factor authentication, it’s likely that you will have to start using this for many platforms in the years to come. Multi-factor authentication is the future of passwords.
Social engineers work by manipulating your needs and emotions. The last thing they want is for you to sit back, take emotions out of the equation, and apply cold logic to the situation.
So, they will often try and ramp up the urgency so that you don’t stop to think. For example, a scammer using scareware might say you need to click a link within the next five seconds, or your phone will be wiped. Or a scammer posing as a loved one might say that they need you to send money RIGHT NOW or they will miss an urgent flight.
Don’t fall for it. Verify the identity of the person and/or the truth of what they are saying before you click any link, enter any details, or send any money.
Avoiding social engineering attacks is one of many great reasons to get a trustworthy VPN.
Everything you do on the internet adds to your ‘digital footprint’. You can cover your tracks, however, with a good VPN.
A VPN helps keep social engineering attacks away by hiding you from the perpetrators. If you can’t be tracked through the Internet, you make a much harder target.
Unless a scammer has a particular interest in you specifically, they are unlikely to go for complex targets. Most scammers cast a wide phishing net in the knowledge that many people will be able to escape it. They rely on catching enough easy targets to make things worth their while.
If you make yourself a tough target, they’re unlikely to waste much time trying to scam you. A VPN is an excellent way to make yourself just such a tough target.
It’s especially important to get a VPN for traveling. As you move through different systems and networks, you can become visible to different kinds of scammers. A VPN will protect you from this.
Avoiding social engineering attacks isn’t like installing a filter to protect your workflow orchestration software from bots. Social engineering attacks don’t go for your software. They go for your emotions.
Advanced cybersecurity measures, like biometric authentication and a VPN can help you against social engineering attacks. But the best way to protect yourself is to keep a cool, calm head and think critically whenever asked for money, or passwords, or sensitive information.
Don’t automatically trust anyone on the internet - no matter how well you think you know them. Whenever someone asks you for something sensitive, take a step back and think hard about what they’re asking.
Then, take steps to verify their identity outside of the ‘bubble’ they may have set up.
For example, if you get an email purporting to be from the IRS asking for sensitive employee data, don’t reply to the email asking for more information. Instead, phone the IRS and talk to them directly about this.
By operating on this low-trust, critical, logical basis, you can protect yourself and your business from even the most insidious social engineering attacks.
Autor's Bio:
Jessica Day is the Senior Director for Marketing Strategy at Dialpad, a call routing service provider and a modern business communications platform that takes every kind of conversation to the next level—turning conversations into opportunities. Jessica is an expert in collaborating with multifunctional teams to execute and optimize marketing efforts, for both company and client campaigns.