When you browse the web, you may come across a variety of online threats. And these threats aren't limited to malicious websites. If you're not careful, you could accidentally infect your computer with malicious software even when visiting the most legitimate of sites.
But how's that possible? In a word, malvertising.
Malvertising (malicious advertising) is a relatively new cyberattack technique that inserts malicious code into digital advertisements. These infected ads are usually served to consumers through legitimate advertising networks, making them difficult to detect by both internet users and publishers.
The advertisements appear tempting, genuine, and to be from a trustworthy source. The host website owner may not even be aware that malvertising is being displayed on their site.
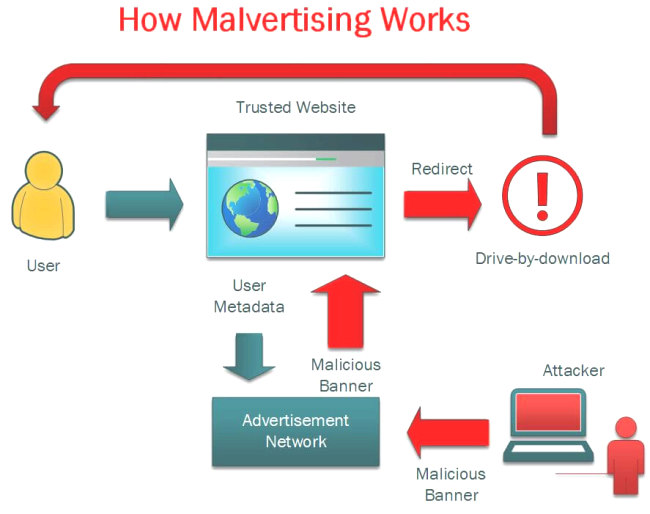
Because the world of online advertising has become so diverse, cyberattackers have responded with a variety of malvertising scam strategies. So, ensure that you’re well-versed in cybersecurity and its best practices.
To help you understand these attacks, here are some of the more common types of malvertising.
Steganography is the art of concealing secret messages within text or images. Many malvertising attacks use a modern form of steganography to conceal malware within advertising images.
Hackers only need to change a few pixels to make the difference hidden to the naked eye. The code can then be used to directly infect your device or initiate subsequent stages of an attack.
Polyglot images are a more sophisticated cousin of steganography. Not only do they contain malicious code, but also the scripts required to execute that code and launch the attack. That's where the name comes from: the images can "speak" multiple languages rather than just concealing one thing at a time.
This method involves tricking you into believing there’s a technical problem with your device. The fraudulent ads will typically install browser hijacker malware to disrupt your user experience before instructing you to call a number to resolve your fictitious problem.
Tech-support scammers pose as representatives of reputable companies and attempt to extract money and personal information from you to "fix" the bogus problem.
Scareware, like the tech-support scam, tries to frighten you into believing your computer has a problem - in this case, that you've been infected with a virus or some other form of malware.
A pop-up will appear, informing you that malware has been detected and urging you to download their "solution". Scareware software is always useless, and in some cases may even be malware itself.
The internet is littered with advertisements for shady "get rich quick" schemes and phony surveys.
For example, if a marketer is looking for free premium tools for affiliate marketing, it can be very tempting to visit websites that promise large payouts or benefits. These websites may ask you to leave a review or complete some other insignificant task.
Any advertisement with an offer that appears too good to be true most likely is.
Scammers display their ads on legitimate websites using third-party ad distributors such as Google Ads, Propeller Ads, and others. This is how they are able to get their ads on well-known and trusted sites.
The perpetrator, like any other advertiser, creates a free account on such sites, creates some malware-filled advertisements, bids on keywords, and specifies the daily budget and target audience.
Cybercriminals sometimes steal legitimate advertisements from well-known companies to make them hard to spot. However, instead of linking to legitimate organizations, they link to their malicious websites.
Some companies may choose to rent out space on their website to advertisers instead of joining a third-party ad distribution network.
Initially, these attackers would generally place harmless ads, and after gaining the trust of the company, they begin adding malware in the ads.
This outdoor advertising displayed on rented spaces can take the form of ad banners, text ads, videos, or even sponsored articles.
Some hackers manipulate websites with poor security postures to display malicious advertisements. The affected website owners have no idea that their websites are showing such ads.
So, for your own safety, the next time you're looking for a service for your company, like email tracking software or virtual communication tools, make sure to confirm the website has an SSL certificate.
Imagine a user is browsing a site and they are warned it’s hosting malvertising. They will likely then avoid that website in future because they believe it to be unsafe. The result: the business’s bottom line suffers.
A reputation for hosting bad ads can hurt not only a publisher's traffic but also any publisher's or platform's efforts to strengthen relationships with business partners.
You may be wondering what will happen if you do click on a malvertisement. Let's look at how attackers can defraud you using malvertising with some hypothetical examples.
Malvertisements are commonly used to spread malware such as viruses, worms, trojans, and root-kits. Infected advertisements install malicious codes or software on website visitors' devices, allowing them to launch various cyber-attacks against them.
Example: Elissa is surfing the web for how to effectively track SEO results. She sees an advert saying, “80% Off Guaranteed SEO Tool!”.
She clicks on the ad, which takes her to a legitimate-looking website. When the page loads, it displays a message saying, “Sorry, this service is temporarily unavailable.”
Elissa closes the tab, disappointed, and continues her search. But Elissa is unaware that she has unintentionally downloaded a dangerous virus onto her device.
This quickly crashes her entire system and steals all of her personal information!
In phishing attacks, the attacker impersonates a legitimate entity or person to defraud users. Phishing can occur through emails, phone calls, SMS, Wi-Fi routers, websites, and other means. These websites trick users into downloading and installing malicious software or steal personal/financial information.
Example: Esther is going through a website development proposal template online when she receives a notification that Jennifer has a 40% discount policy on her “website design consultation service” for the first 15 sign-ups.
Esther is a regular customer of Jennifer's, so she obviously wants to take advantage of this offer. She clicks on the ad, navigates to what she believes is Jennifer's website, and completes a form.
Esther receives notification that Jennifer will confirm her booking shortly. She has no idea that the website she used to fill out the form was a phishing website that looked exactly like Jennifer's original site.
And instead of Jennifer, the hackers have received all of her information and they will soon make her a victim of identity theft or financial fraud!
Some malvertisements download malware onto website visitors' devices even if they don’t click on anything or press the download button. This type of malware is known as drive-by malware because it automatically downloads without user action. Malvertising is one method by which drive-by malware spreads.
Example: Will runs a successful health and fitness blog that receives over a thousand website visitors per month. Will was surprised when he received an angry email that read, "CAN YOU PLEASE STOP SPREADING VIRUSES!"
But it didn't end with just one email. Within 72 hours, he received more than 100 such angry emails, complaining about "suspicious software downloads".
What Will doesn't realize is that the person paying him $70 per month to publish a small pharmacy advertisement on his blog is a hacker and behind all of this.
He inserted drive-by malware into the blog through advertisements. Then when a website visitor visits Will's blog, they unintentionally download drive-by malware to their devices.
The first line of defense against malvertising will be antivirus, antimalware, and anti-spyware software. These tools will notify you if anything downloads to your device. Furthermore, they will scan all downloads and installations, and remove any known malware.
If you’re redirected to a website, carefully examine the URL to ensure you’re on the official website of the company.
Imagine you’re new to the business world and want to know how to apply for an EIN online, make sure you check whether the company's web address is real or if the information is suspicious or too good to be true.
You should also try a separate Google search to ensure you are going to the right address. Click on the padlock symbol in the address bar to verify the website's and organization's information in its SSL/TLS certificate. Of course, if the site isn't using one of these certificates that should raise a red flag.
You should take the time to ensure you constantly monitor, scan, detect, and remove malicious codes from your website using website scanners.
This means if a problem does arise, like your site being infected with malware, you will be notified and advised on the best course of action to clean up and protect your site.
Most of these tools can also remove viruses, malware, and other security threats that may be compromising your website. Finding and removing these yourself will be nearly impossible unless you are a security expert. Also, make sure you keep your browser and plugins up to date.
Using a comprehensive ad-blocker is a simple and effective way to prevent malware from reaching you through advertisements. This will prevent both legitimate and fraudulent ads from appearing on your screen, denying malicious code access to your system.
Using a VPN can also stop people, software, and web browsers from gaining access to your network. For example, an application or website can track your online activity without your knowledge. They can then analyze the information they have gathered and use it to target you with advertisements.
Without a VPN you may encounter an influx of pop-up ads, which can disrupt your browsing experience.
Only download media players, browser extensions, or updated versions of any applications from their official websites. For example, if the software you're trying to download indicates that it needs the most recent version of Chrome, only download it from the official Chrome website.
Instead of clicking on an ad that claims your system is infected with a virus, scan your device with a trusted antivirus or anti-malware software instead.
In general, we advise people to avoid malicious websites and to avoid downloading anything that appears suspicious. However, in malvertising, the host websites are reliable, and the ad content frequently appears to be harmless.
So, even the most vigilant people fall victim to such attacks. As a result, robust security software is the best way to warn you when you are downloading infected material from the internet.
Using strong passwords, keeping all of your software components up to date, and using ad-blocking software can also be beneficial. If you receive malware-related complaints from website visitors, take their concerns seriously and scan all of your advertisements. If you use third-party ad platforms, contact them right away to report the problem.
Author's Bio:
Sam O’Brien is the Chief Marketing Officer for Affise—a Global SaaS partner marketing program. He is a growth marketing expert with a product management and design background. Sam has a passion for innovation, growth, and marketing technology. Sam O'Brien also published articles for domains such as Demio and VWO. Here is his LinkedIn