<< All posts1 October 2025
With technology – smartphones, tablets, laptops, etc. – being used more and more worldwide, it’s no wonder there are many more public and guest Wi-Fi hotspots than in previous years.
But, with more convenient Wi-Fi hotspots there are possible security risks, where personal information can be stolen and exposed without you knowing it. Without adequate protection, you’ll risk exposing your online identity and money to online hacks.
With that said, here are 8 effective ways to stay safe, should you plan to use public Wi-Fi. read more...
1 July 2025
The rate at which folks visit adult websites is on the upward trajectory, and the trends show no signs of stopping any time soon. According to report, adult websites are more popular than Amazon and Netflix. But here’s the point: as much watching adult content is often discussed in a morality context, a huge elephant in the house is usually overlooked – security and privacy.
If you think that you will never be affected by such issues, this could be the right time to reconsider. read more...
6 February 2025
DeepSeek AI, a rapidly emerging Chinese artificial intelligence platform, has been recently at the center of multiple security incidents and growing scrutiny from international authorities. These developments have raised significant concerns about the platform's data handling practices and overall safety.
In response to these security concerns, several governments and organizations have taken precautionary measures.
If you decide to use DeepSeek AI despite its security concerns, using a trusted VPN is highly recommended to safeguard your privacy read more...
5 February 2025
TrustZone VPN is stepping up its security game for the future by introducing post‑quantum encryption in 2025.
But what does that mean for you, the everyday user?
Simply put, this upgrade is designed to keep your online data safe - even when powerful new computers, called quantum computers, come into play.
Post‑quantum encryption is a new kind of security technology designed to be strong enough to withstand attacks from quantum computers. It uses advanced mathematical methods that even the next generation of computers will struggle to break. This means your data will remain private and secure, no matter what technological advancements come next. read more...
3 January 2025
The moment you connected your computer to the Internet, you placed it on the 'cyber' battlefield. You might not want to fight in a cyber war, you probably just want to browse the web and check Facebook in peace, but simply by connecting your computer to the Internet, you have placed it, and everything on it, 'in harm's way'.
Would you send a soldier off to battle without body armor? No, so don't send your computer out into the fray unprotected. The enemy doesn't care what country you claim as your own, they don't care that behind the screen is a 65 year-old grandmother who loves to knit sweaters and watch funny cat videos.
So ask yourself the question: Is my computer ready for battle? read more...
18 January 2024
Hackers don’t limit their attacks to e-commerce sites. Blogs are vulnerable as well. WordPress and other suites are so popular that cybercriminals make it their business to learn how to exploit any weaknesses.
When they find those openings, they might take your site hostage, redirect your visitors to nefarious websites, or retrieve sensitive data about your business or customers.
In any case, it’s imperative that you ensure your blog is locked down. You can start this process by checking out the following security tips. read more...
13 July 2023
Everybody knows that cybersecurity plays a pivotal role in safeguarding our online existence. It is imperative to adopt proactive measures that shield us from potential threats. With the relentless surge in cyber attacks, bolstering our cybersecurity awareness has assumed paramount importance.
Let's delve into 15 invaluable tips that will empower you to fortify your online safety, ensuring the utmost protection for your sensitive information. read more...
20 March 2023
VPN is an effective tool for remote work but is frequently misunderstood to be the ultimate protector of online privacy. VPN won't make you completely anonymous online, but it can make your surfing more secure and flexible.
Read more to learn about trusted VPN services and how it can help you with your data security. read more...
19 January 2023
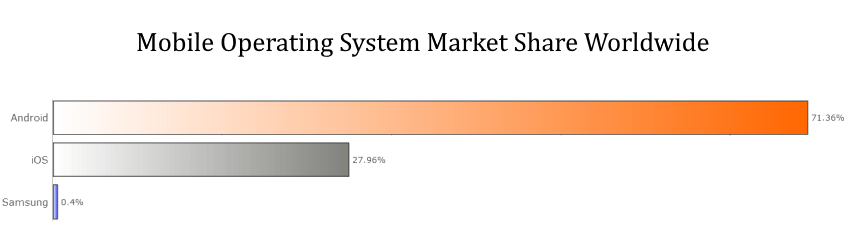
When you are looking to enhance the security of your personal smartphone the results can be very different depending on which operating system you are using.
Yes, because despite ever-improving technological advances that help to strengthen security, cyber criminals are also keeping up and attacking our data and networks in a myriad of novel and elaborate ways.
Therefore, if you want to stay ahead of the game, it’s time to review two of the most popular operating systems in the world and find out which one is the best and most secure, both for your personal data and for your business.
Who is the winner of the all-time OS security war — Apple or Android? Learn more in our comparative guide. read more...
21 December 2022
Businesses deal with a lot of confidential information daily. Whether it's customer data, financial reports, or trade secrets, companies must ensure that this information stays confidential.
One way to do this is by implementing best practices for securing confidential business information. These practices can help protect your data from unauthorized access, theft, or misuse. read more...