<< Tüm gönderiler1 Temmuz 2025
The rate at which folks visit adult websites is on the upward trajectory, and the trends show no signs of stopping any time soon. According to report, adult websites are more popular than Amazon and Netflix. But here’s the point: as much watching adult content is often discussed in a morality context, a huge elephant in the house is usually overlooked – security and privacy.
If you think that you will never be affected by such issues, this could be the right time to reconsider. daha fazla oku...
21 Mart 2025
Using a VPN for your home network is a great idea, but business leaders should understand the importance of having a VPN for their corporate network. Now that more and more people are working remotely and that companies are managing network access on numerous fronts, one of the best ways to keep your employees safe online is with a VPN.
But that doesn’t mean that a VPN can’t be exploited, nor does it mean that you shouldn’t complement it with other cybersecurity solutions. After all, a VPN can help you dispel some common cybersecurity myths, while additional security protocols can help keep your VPN network completely secure.
Let’s take a look at what these are and what you can do to prevent your VPN from getting hacked. daha fazla oku...
18 Ocak 2024
Hackers don’t limit their attacks to e-commerce sites. Blogs are vulnerable as well. WordPress and other suites are so popular that cybercriminals make it their business to learn how to exploit any weaknesses.
When they find those openings, they might take your site hostage, redirect your visitors to nefarious websites, or retrieve sensitive data about your business or customers.
In any case, it’s imperative that you ensure your blog is locked down. You can start this process by checking out the following security tips. daha fazla oku...
16 Eylül 2021
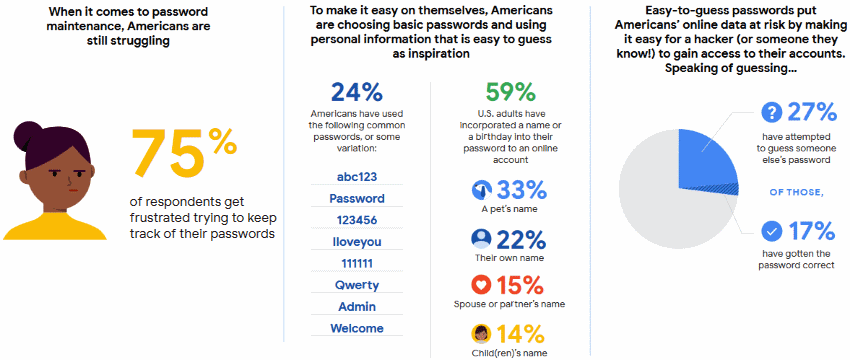
One of Google’s study with Harris Poll revealed the real truth behind passwords creation of native Americans. The vast majority faces frustration and even difficulties when coming up with a password. Having no secure strategy in mind and lacking an operating system to ensure that password verification has the latest security updates simply makes the American people struggle - nearly 75%
The five most popular of which are: 123456, Password, 12345678, qwerty, 123456789. daha fazla oku...
17 Haziran 2021
Phishing websites are tools that cybercriminals use to steal personal information. They trick people into disclosing their passwords, phone numbers, credit card details, etc.
For example, phishing websites can mimic Netflix and ask you to update your payment details or require you to log in to your PayPal account to update information. daha fazla oku...
15 Şubat 2021
Online scams are more common than you might think. Just because you are aware of the potential threats and have taken the necessary measures, it does not mean that other people have done the same.
No, there are plenty of individuals who end up making poor decisions and suffer for it by having their personal data exposed. More people should pay attention to their activities online. Hopefully, the tips mentioned below should help prevent scams online. daha fazla oku...
8 Şubat 2021
One of the most incredible things about MacBooks is its unique security system. We want to talk about the security system itself, which takes care of the entire system and keeps all the devices attached to your MacBook save.
Here are the 5 most effective tips to protect your MacBook from hackers daha fazla oku...
3 Şubat 2021
If you have an email account, use Facebook, Twitter, download iTunes, or do anything on a computer that is connected to the Internet, you too could be hacked.
Here are things you should do if someone has stolen account information, or you receive a warning notice an account has been hacked. Even if you have not been hacked, many of these steps can help protect you in the future. daha fazla oku...
12 Aralık 2020
Hackers have been all over the news lately, whether it’s a major hacker collective, a lone wolf hacker, or some “script kiddies” just hacking for the thrill of it, hackers seem to be hitting us from all angles.
Are there any defenses against the savvy hacker or even the amateur one?
Let’s look at several things that hackers hate to see a target have in place as security measures: daha fazla oku...
20 Kasım 2020
It wouldn’t be wrong to say that digital adoption increases digital risk.
Ransomware is a very common security threat distributed by criminal-minded cyber offenders through phishing emails or online downloads that usually have malicious code. As soon as the infection begins, the legitimate owners lost access to their sensitive data. Your access will be renewed only if you pay a fee. daha fazla oku...