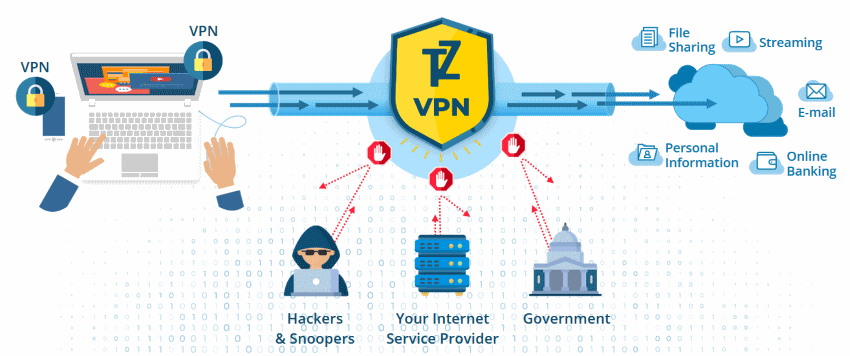
VPN ensures that the users can work on a private network and not have a fear of compromise. But beyond just protecting your privacy on the internet, there are other ways to maximize your VPN.
Here are 9 ways to optimize your VPN use. leer más...

VPN ensures that the users can work on a private network and not have a fear of compromise. But beyond just protecting your privacy on the internet, there are other ways to maximize your VPN.
Here are 9 ways to optimize your VPN use. leer más...

With technology – smartphones, tablets, laptops, etc. – being used more and more worldwide, it’s no wonder there are many more public and guest Wi-Fi hotspots than in previous years.
But, with more convenient Wi-Fi hotspots there are possible security risks, where personal information can be stolen and exposed without you knowing it. Without adequate protection, you’ll risk exposing your online identity and money to online hacks.
With that said, here are 8 effective ways to stay safe, should you plan to use public Wi-Fi. leer más...

Can you spot a phishing email if you receive one? Scammers often send emails or text messages to victims in an attempt to trick them into disclosing sensitive information.
And if you're not paying attention, you can get hooked. So what is phishing and how to avoid it? leer más...

Using a VPN for your home network is a great idea, but business leaders should understand the importance of having a VPN for their corporate network. Now that more and more people are working remotely and that companies are managing network access on numerous fronts, one of the best ways to keep your employees safe online is with a VPN.
But that doesn’t mean that a VPN can’t be exploited, nor does it mean that you shouldn’t complement it with other cybersecurity solutions. After all, a VPN can help you dispel some common cybersecurity myths, while additional security protocols can help keep your VPN network completely secure.
Let’s take a look at what these are and what you can do to prevent your VPN from getting hacked. leer más...

Did you know that Trust.Zone support the latest Military-Grade Encryption algorithm - AES-256 encryption?
AES256 is a symmetrical encryption algorithm. It is otherwise known as “military-grade encryption” because it is adopted by the U.S. and Canadian governments as standards for encrypting transited data and data at rest. Because of the 256-Bits length of the key and the number of hashes (14), it takes a long time for a hacker to perform a dictionary attack leer más...
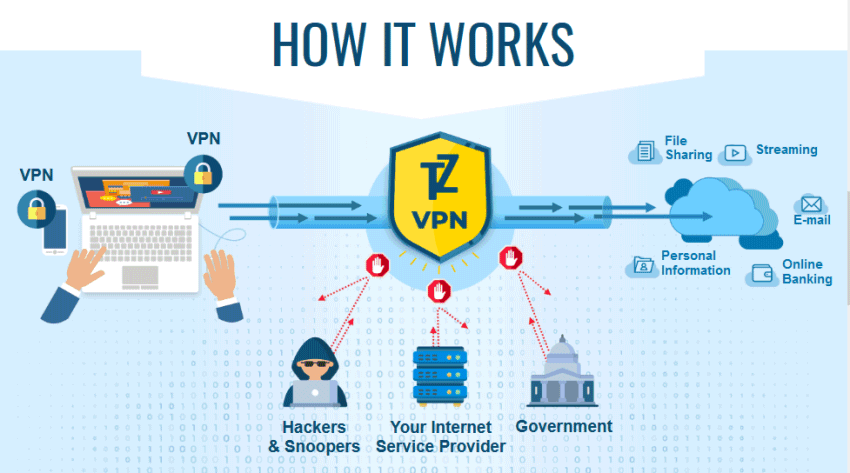
You’ve no doubt heard the term VPN before. This is hardly surprising; consumers and businesses are becoming increasingly aware of how important their privacy is and the need to protect their data. This awareness has, in part, grown due to the rise in cyber-attacks and data breaches in recent years.
What’s more, cybercrime is expected to increase in the coming years, with its cost estimated to reach 17.65 trillion US dollars in 2025.
For this reason, many turn to security tools such as VPNs to protect themselves from cybercrime. This article will take you through what a VPN is, how it works, and how exactly it helps with data protection. leer más...

Using public wifi is convenient, especially when you're out of the house and don't want to use your valuable data. However, logging in to a public network isn't as safe as surfing the internet at home.
Cybercriminals will often target public hotspots as a way of accessing devices with weak security measures.
Lets dive into how VPN technology can help protect you, so you can continue surfing on public Wi-Fi. leer más...

When running a business, you can’t expect everything to go as smoothly as planned. Sometimes, you’ll encounter difficulties along the way that can affect processes and your revenue.
There’s also the threat of cybercriminals using unethical ways to seal your information, leading to significant issues like identity theft. Cybercriminals often gain access to sensitive information via system vulnerabilities which lets them take over accounts, steal sensitive data, and make unauthorized transactions.
That’s why you need to be vigilant at all times and use identity management solutions to prevent these events from happening. It would be best if you always stayed vigilant at all times.
We’ll walk you through the nine smart ways to protect your customers from identity theft: leer más...

Data protection is becoming increasingly difficult for businesses and individuals. Is this difficulty due to the lack of knowledge among individuals and businesses about protecting their data, or is hacking an increasingly popular activity? Whatever the case, online security is a must.
The more data you need to protect, the more influential the act of data protection becomes.
Let’s discuss six essential tips you must follow to protect your data on the highest level. leer más...

The ultimate aim of a blockchain is to manage the secure and transparent recording and distribution of data by reducing the likelihood of data leaks. This makes blockchain tech the building block for immutable online activities.
Blockchain tech offers one of the most robust data protection systems out there. This helps reduce the occurrence of fraudulent activities and data theft.
Blockchain gives you confidence in the security of your data and online transactions, so it’s not surprising that global spending on blockchain solutions is projected to rise in the next few years.
The more users on the network, the harder it is to corrupt the system. Large blockchain networks face a low risk of cyberattacks for this reason. leer más...