<< Alle Beiträge12 Juni 2025
When you can find any kind of information just in a couple of minutes, you think you’re all-powerful. Actually, it makes you really vulnerable. Tech companies and Internet Service Providers sell your personal information off to the highest bidder. And it is not the only danger when you’re online. weiterlesen...
1 April 2025
Since there are lots of VPN uses that you might not be aware of, we’re going to highlight five uncommon uses for a VPN and how it works in your favor most of the time. weiterlesen...
18 Januar 2024
Hackers don’t limit their attacks to e-commerce sites. Blogs are vulnerable as well. WordPress and other suites are so popular that cybercriminals make it their business to learn how to exploit any weaknesses.
When they find those openings, they might take your site hostage, redirect your visitors to nefarious websites, or retrieve sensitive data about your business or customers.
In any case, it’s imperative that you ensure your blog is locked down. You can start this process by checking out the following security tips. weiterlesen...
5 Oktober 2023
What comes to mind when you hear the word VPN? As the name implies, this service provides online anonymity, privacy, and protection. As such, it’s best to keep up with the VPN trends and hire a highly reliable service provider.
But nothing can be more frustrating than your VPN frequently disconnecting and reconnecting. Why is this happening in the first place?
There are various reasons for this! However, getting to the bottom of the problem and fixing it can be tricky and often frustrating.
Don’t worry; this guide shares with you how to handle VPN connection drops. Keep reading to earn tips and tricks for addressing these fluctuating issues and ensuring online protection. weiterlesen...
13 Juli 2023
Everybody knows that cybersecurity plays a pivotal role in safeguarding our online existence. It is imperative to adopt proactive measures that shield us from potential threats. With the relentless surge in cyber attacks, bolstering our cybersecurity awareness has assumed paramount importance.
Let's delve into 15 invaluable tips that will empower you to fortify your online safety, ensuring the utmost protection for your sensitive information. weiterlesen...
13 Januar 2023
Data protection is becoming increasingly difficult for businesses and individuals. Is this difficulty due to the lack of knowledge among individuals and businesses about protecting their data, or is hacking an increasingly popular activity? Whatever the case, online security is a must.
The more data you need to protect, the more influential the act of data protection becomes.
Let’s discuss six essential tips you must follow to protect your data on the highest level. weiterlesen...
17 November 2022
As the workplace becomes more digital, your employees should have appropriate skills to be safe when surfing the internet. Your employees should know the risks and steps to take to protect themselves from cyber-attacks.
To be secure online, you must constantly educate your staff and make changes following technological advancements. Also, you may consider the help of a company with IT support services to clean up your computer network, eliminate potential problems, and help your team implement efficient technology. Having said that, the following are some internet safety tips you can implement in the workplace: weiterlesen...
9 November 2022
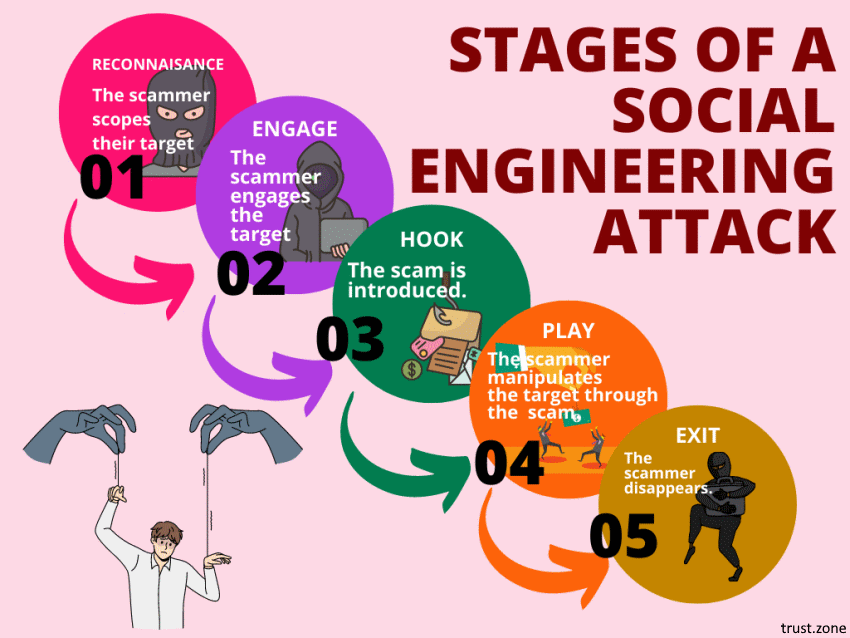
Social engineering attacks are on the rise. In fact, they’re among the most successful and insidious types of cybercrime active today.
Worst of all, you can’t protect yourself from all social engineering attacks by just boosting your computer security. A good social engineering attack doesn’t target your software. Instead, it targets the human element. It tries to trick you, often by playing on your emotions. Social engineering attackers are scammers who use human emotions as the tools of their trade.
To protect yourself from social engineering attacks, you need to secure your mindset as well as your technology. Let us show you how. weiterlesen...
24 Juli 2022
While you may believe that your site doesn't have anything worth hacking, you'd be surprised how many websites are vulnerable to hacks.
Many website security breaches happen not to steal your data or mess with your layout. It uses your server as an email relay for spam and sets up a temporary server, which serves illegal files.
Another common way to abuse compromised machines is using a server as part of the botnet or mine for Bitcoins. Similarly, you can be hit by ransomware as well.
Hacking can be done by automated scripts that scour the internet to exploit a software’s known security problems. That’s why, in this post, we’ll talk about the eight practical tips on how you can keep your database safe and secure online: weiterlesen...
4 Mai 2022
We could talk for hours about the larger socio-political issues that social media has a hand in, but what about the more immediate dangers closer to home? What about the glaring risks to our personal privacy?
In the attempt to connect people internationally, social media devs have inadvertently put some very dangerous tools in the hands of hackers, stalkers and a myriad of other cyber criminals.
In the interest of preventing your information from being accessed by these types of people, we’ve compiled a list of 5 tips and best practices to help you insure you’re using social media safely and securely. weiterlesen...