<< Все статьи18 Мая 2021
Once you turn a computer on and connect it to anything, including your USB thumb drive, it is exposed to threats. Because of the nature of data movement methodologies and personal habits, there are threats everywhere. Know this and accept that fact and you have the right mindset to be safe.
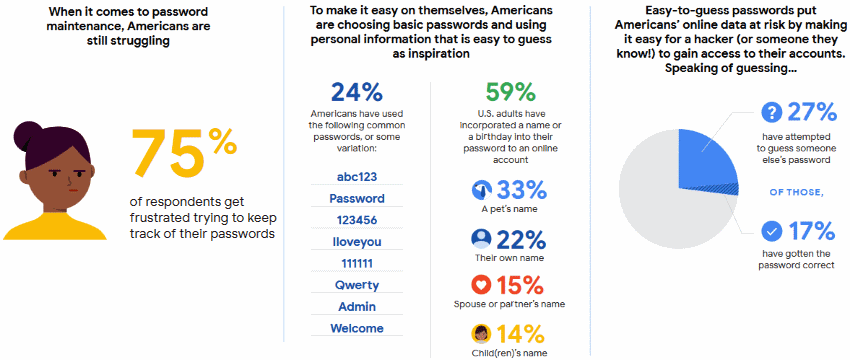
The Internet is a vast and cool place, but as with everything good, there is a counterculture who wants to exploit it for their motives. In a way, a healthy dose of paranoia is good when computers are involved. The first preventative is a password.
We have decided to create a simple guide on how to make your password strong. подробнее...
13 Апреля 2021
Since digitalization becomes a massive part of our life and the process fastens because of pandemic outbreaks in 2020-2021, more and more businesses proceed with remote working. In turn, remote work widens the list of potential risks for employers and requires more cybersecurity.
Being a skilled cybersecurity specialist after getting a quality education in this area, you can earn from USD 80,000 to 160,000 per year (the average salary for a cybersecurity analyst position in the US.) подробнее...
17 Марта 2021
As more people are online, this is an open door for hackers to find cybersecurity weaknesses and attack them. More people mean more targets, and this is something hackers have done during this pandemic. However, the past year taught us important lessons regarding cybersecurity which we need to pay attention to this year too. подробнее...
9 Марта 2021
No one will forget the major cybersecurity breaches that made international news – the U.S. IRS, Pentagon, and State Department, the retailer Target, and the credit reporting enterprise, Experian. These made international news because of the sheer size of these organizations and the number of people whose personal information was compromised.
No matter what size your business is, you must have strong enterprise cybersecurity systems of course, and, just as important, develop a policy that regulates the behaviors of everyone within the organization as well as any outside individual or organization doing business with your organization. подробнее...
15 Февраля 2021
Online scams are more common than you might think. Just because you are aware of the potential threats and have taken the necessary measures, it does not mean that other people have done the same.
No, there are plenty of individuals who end up making poor decisions and suffer for it by having their personal data exposed. More people should pay attention to their activities online. Hopefully, the tips mentioned below should help prevent scams online. подробнее...
12 Февраля 2021
Working from home is not simple. Sure, you could argue that there are those who thrive because they do not have to commute to work every day and can spend more time relaxing.
However, one cannot underestimate the importance of surrounding yourself with an environment that motivates and encourages productivity. Here is a list of 5 ways technology can improve your work productivity подробнее...
8 Февраля 2021
One of the most incredible things about MacBooks is its unique security system. We want to talk about the security system itself, which takes care of the entire system and keeps all the devices attached to your MacBook save.
Here are the 5 most effective tips to protect your MacBook from hackers подробнее...
3 Февраля 2021
If you have an email account, use Facebook, Twitter, download iTunes, or do anything on a computer that is connected to the Internet, you too could be hacked.
Here are things you should do if someone has stolen account information, or you receive a warning notice an account has been hacked. Even if you have not been hacked, many of these steps can help protect you in the future. подробнее...
21 Января 2021
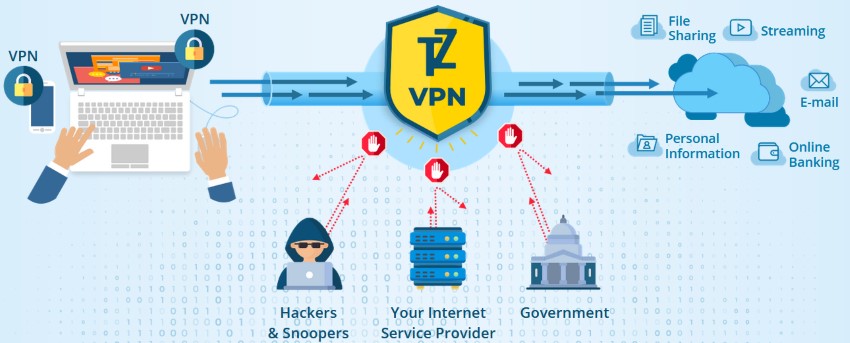
With big opportunities come big responsibilities. You are not only consuming data, but you also share it, and that's why being online may be dangerous for you, especially when you're connected to public Wi-Fi that can be easily hacked. But even at home, you can't just relax before you're completely sure that you're not vulnerable.
It is time to understand why VPN is important and how to get the most out of it. подробнее...
10 Января 2021
A BYOD (Bring your own device) policy provides both opportunities and challenges for the business organization. But by following the right practices, organizations can leverage the advantages and make BYOD a valuable part of their company.
In this guide, let's take a look at some of the challenges faced by BYOD-following companies and ways to mitigate the effect. подробнее...