<< Все статьи18 Января 2024
Hackers don’t limit their attacks to e-commerce sites. Blogs are vulnerable as well. WordPress and other suites are so popular that cybercriminals make it their business to learn how to exploit any weaknesses.
When they find those openings, they might take your site hostage, redirect your visitors to nefarious websites, or retrieve sensitive data about your business or customers.
In any case, it’s imperative that you ensure your blog is locked down. You can start this process by checking out the following security tips. подробнее...
1 Января 2024
Final Call – Sale Ends Today: Enter promo code "EXTRA" on checkout and get extra 6 Months for FREE!
Apply coupon "EXTRA: and get additional 6 months for FREE — the total price remains the same!
Hurry! It's a limited time deal.
Only 500 promo codes for TrustZone VPN are available for activation подробнее...
31 Декабря 2023
It's Xmas SALE! It's the Last Chance to grab the best deal of the Year
Hurry to grab the limited deal - Get 1 Year for FREE. Extra 1,000 activations available only
With TrustZone VPN, experience full online privacy and security that keeps your data hidden from unwanted attention.
Don’t miss out - the limited Xmas deal is available until all activations are claimed! подробнее...
7 Декабря 2023
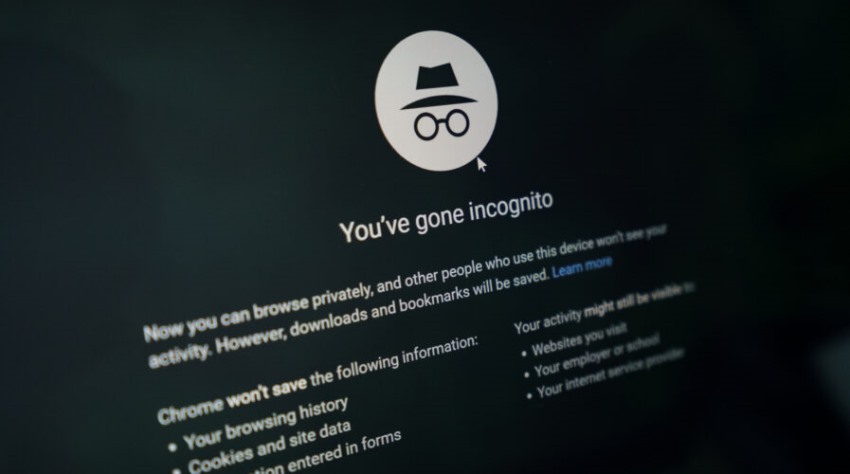
In an era dominated by digital footprints and data trails, internet users are increasingly concerned about their online privacy. As a response to this growing apprehension, web browsers have introduced a feature known as "private browsing" or "incognito mode."
This mode promises to provide a secure and private online experience, but is it truly as confidential as it seems? подробнее...
1 Декабря 2023
Halloween magic is already in the air!
Find your treats with our special deals. Get your thrilling savings NOW!
Get 6 months of FREE VPN protection and stay safe from the scariest threats online. подробнее...
29 Ноября 2023
Web Real-Time Communication (WebRTC) is an open-source technology in today's digital landscape. It allows real-time data exchanges and user interactions via web browsers and devices.
With this feature in place, you can easily and quickly communicate with other users via text, audio, or video without needing an intermediate server. Amazing, isn't it?
But here's the problem: WebRTC can expose your IP address, not to mention your network interface, operating system, and web browser. This leak happens when the Session Traversal Utilities for NAT (STUN) looks for the best path for data transmission. Even if you're using a VPN, WebRTC leaks can still occur. Scary, right?
Beware: WebRTC leaks can be a huge concern for your online privacy and security. подробнее...
10 Ноября 2023
Why Wait Until November?
It's Early Bird - Black Friday right now
Get 6 months for FREE on Trust.Zone VPN plans. Ends Today подробнее...
25 Октября 2023
New Year Sale Ends Today!
New Year Deal from Trust.Zone is ending soon - Get 6 months of TrustZone VPN for FREE
Save up to 80% OFF with TrustZone VPN. Get 2 Years Plan + 6 months FREE for only $1.85/mo. подробнее...
23 Октября 2023
Trust.Zone has announced a significant price reduction of over 50% for dedicated IP addresses for a limited time only. This price drop is set to disrupt the VPN industry, offering customers unbeatable value and flexibility.
Starting immediately, every dedicated IP address will come at a single, uniform price, regardless of its geographic location. This bold pricing strategy aims to simplify and democratize access to dedicated IP addresses.
The limited time offer
Keep in mind that the deal is available limited time only. We only have a limited selection of addresses at a discounted price. Hurry подробнее...
9 Октября 2023
The internet has transformed our access to information and entertainment, connecting people from every corner of the world.
However, geo-blocking by content providers and websites can be an inconvenience. Virtual Private Networks (VPNs) offer a way around this issue, so users can gain access to geo-restricted websites, streaming services, or the content they wish to view.
We will discuss in this article how VPNs can help bypass geo-blocking to allow users to gain access to the content they desire. подробнее...