<< Toutes les publications6 juin 2024
It's a tough reality, but cyber attacks aren't letting up any time soon.
You’ll learn some cybersecurity challenges to expect in 2025 and how you can keep yourself protected.
Here are top 4 cybersecurity challenges in 2025 - 5G security concerns, AI and Machine Learning attacks, IoT security challenges, Social engineering (phishing and etc) en savoir plus...
7 février 2024
In the vast world of the internet, there's a sneaky threat called a replay attack. It's like someone recording your secret handshake and using it to get into places they shouldn't.
Let's explore what replay attacks are, how they work, the risks they bring, and how you can stay safe with a trustworthy VPN en savoir plus...
12 août 2023
Remember that moment when you received an email from your 'bank' urgently asking for your account details? Or perhaps when you clicked on a link, expecting to land on your social media page, only to be greeted with an uncannily similar but subtly off version of it?
If these experiences sound familiar, you've had a brush with the silent but dangerous specters of the internet - phishing websites. Like a detective searching for clues, spotting a phishing website requires a keen eye for detail and understanding their sly tricks.
Let's unravel the key signs that can help you expose these digital impostors. en savoir plus...
13 janvier 2023
Every person or business using the internet will be aware of the danger of cybersecurity threats. We know we can protect ourselves by using different passwords and avoiding suspicious downloads. But cyber attackers are beginning to create more sophisticated ways of exploiting vulnerabilities.
One of the most dangerous threats at the moment is clickjacking. Think about how often you use websites without considering what you’re clicking. While this usually isn’t anything to worry about, clickjacking has created a new threat.
Clickjacking works by placing a malicious set of links over an innocuous-looking website. This means that victims enter passwords or click links that they think are legitimate parts of the original website but are in fact on an invisible page.
This guide will show how you can recognize clickjacking attacks and keep your personal details or business secure. In today’s digital world, protecting yourself from cyber threats has never been more critical, and preventing clickjacking is a crucial part of this. en savoir plus...
8 janvier 2023
Cybersecurity mistakes either happen unintentionally or due to a lack of taking proper action, thus causing a security issue like a data breach. An example of an activity that might cause these errors is compromising your IP address.
Other reasons include clicking an unsafe link, missing updates, and misconfiguration. Businesses and individuals have suffered massive losses and problems due to cybersecurity issues like system disruption and data breaches.
One example of how disruptive these errors can be is a system that has been affected by ransomware. The malware encrypts the files to a point where the original owner can't access their information. en savoir plus...
9 novembre 2022
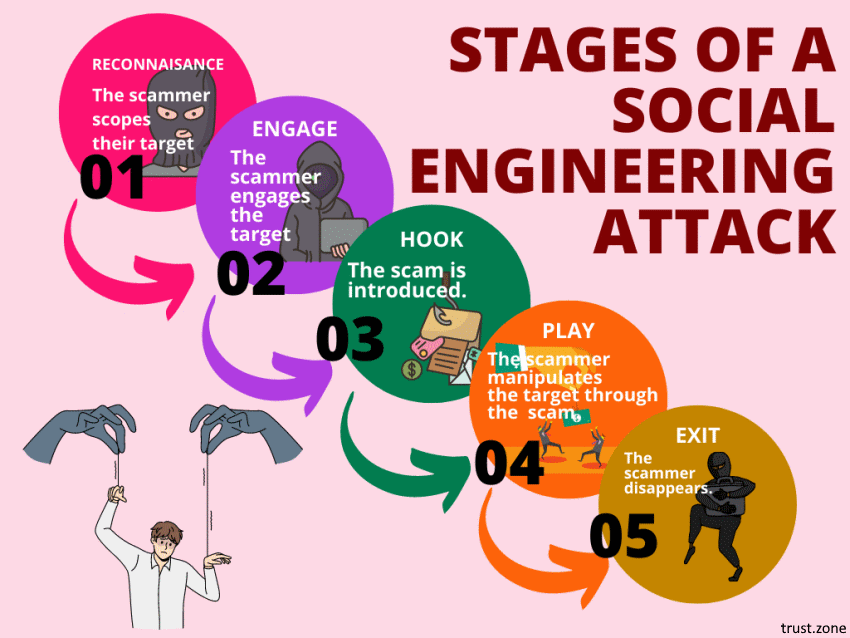
Social engineering attacks are on the rise. In fact, they’re among the most successful and insidious types of cybercrime active today.
Worst of all, you can’t protect yourself from all social engineering attacks by just boosting your computer security. A good social engineering attack doesn’t target your software. Instead, it targets the human element. It tries to trick you, often by playing on your emotions. Social engineering attackers are scammers who use human emotions as the tools of their trade.
To protect yourself from social engineering attacks, you need to secure your mindset as well as your technology. Let us show you how. en savoir plus...
6 septembre 2022
When you browse the web, you may come across a variety of online threats. And these threats aren't limited to malicious websites. If you're not careful, you could accidentally infect your computer with malicious software even when visiting the most legitimate of sites.
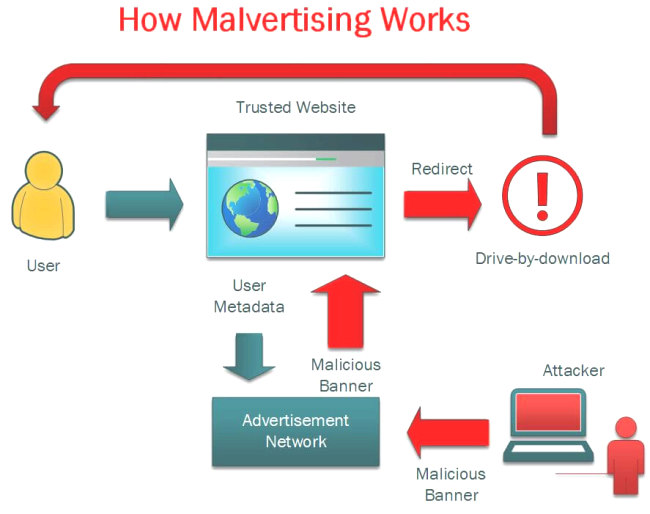
But how's that possible? In a word, malvertising.
Malvertising (malicious advertising) is a relatively new cyberattack technique that inserts malicious code into digital advertisements. These infected ads are usually served to consumers through legitimate advertising networks, making them difficult to detect by both internet users and publishers.
The advertisements appear tempting, genuine, and to be from a trustworthy source. The host website owner may not even be aware that malvertising is being displayed on their site. en savoir plus...
24 août 2022
With so much technology these days, it’s hard for companies and organizations to go without it. Since technology is now the lifeblood of a company, it’s important to keep that blood flowing.
However, cybercriminals are also getting savvy with technology. They’ll launch cyber-attacks on an unsuspecting business and wreak havoc on systems and assets.
Has this ever happened to your company? Or have you feared this for your company? You’re not alone. In just 2021 alone, there were 80,000 cyber-attacks per day – that’s over 30 million attacks annually
Don’t let this happen to your company. Below you will learn of the 6 common mistakes in cybersecurity, and how you can avoid them at all costs: en savoir plus...
3 octobre 2021
According to a recently published 2021 cyber security report, cybercrime went up by 600% during the Coronavirus pandemic. Over the past year alone, more than 500,000 stolen Zoom passwords were posted for sale on dark web forums.
Passwords are one of the most basic and familiar forms of data protection. Yet poor password practices are often the reason behind the billions of breaches and malicious cyber attacks that happen year after year. en savoir plus...
29 juillet 2021
Have you ever wondered what course of action you would choose if your data were to be attacked by ransomware?
Let’s be realistic; though this worst fear of yours has fortunately not manifested yet, you cannot entirely dismiss the possibility of a ransomware attack for a multitude of reasons.
Here are 5 important ways to protect your data when hit by ransomware. en savoir plus...