Terminalemulator ausführen: Drücken Sie Alt+F2 auf der Tastatur, geben Sie x-terminal-emulator ein, und drücken Sie die Eingabetaste.
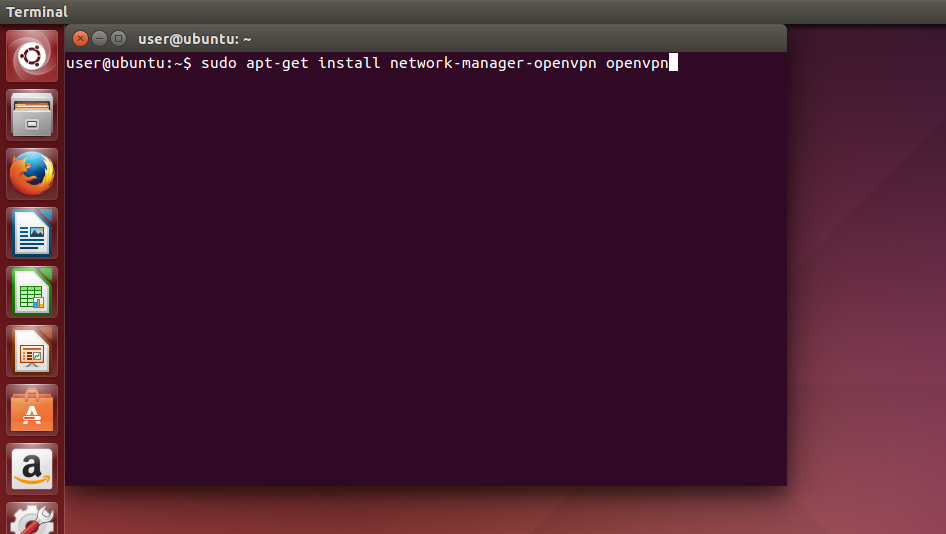
Installieren Sie OpenVPN mit dem folgenden Befehl.
sudo apt-get install network-manager-openvpn openvpn
For Ubuntu 16.04 install also network-manager-openvpn-gnome
sudo apt-get install network-manager-openvpn-gnome
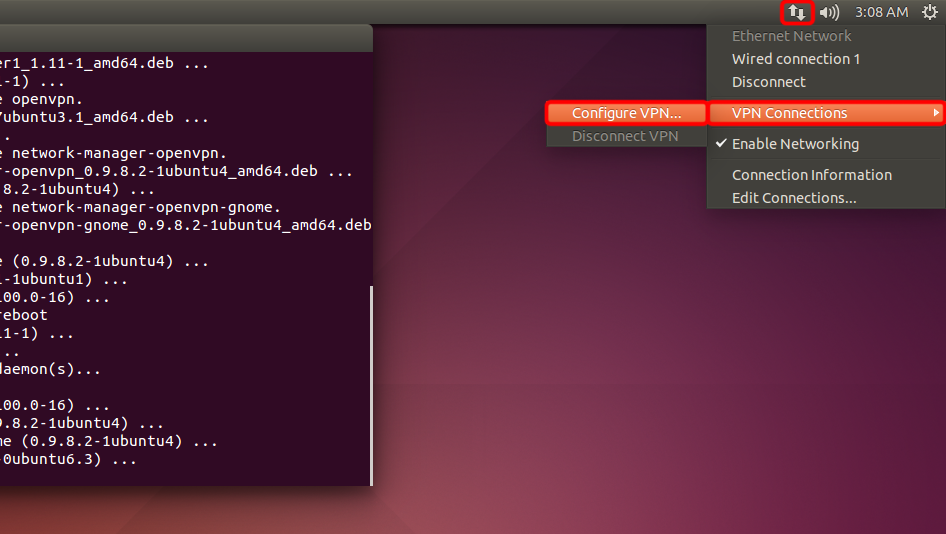
Öffnen Sie das Netzwerkmenü, gehen Sie auf "VPN-Verbindungen" und klicken Sie auf "VPN konfigurieren...".
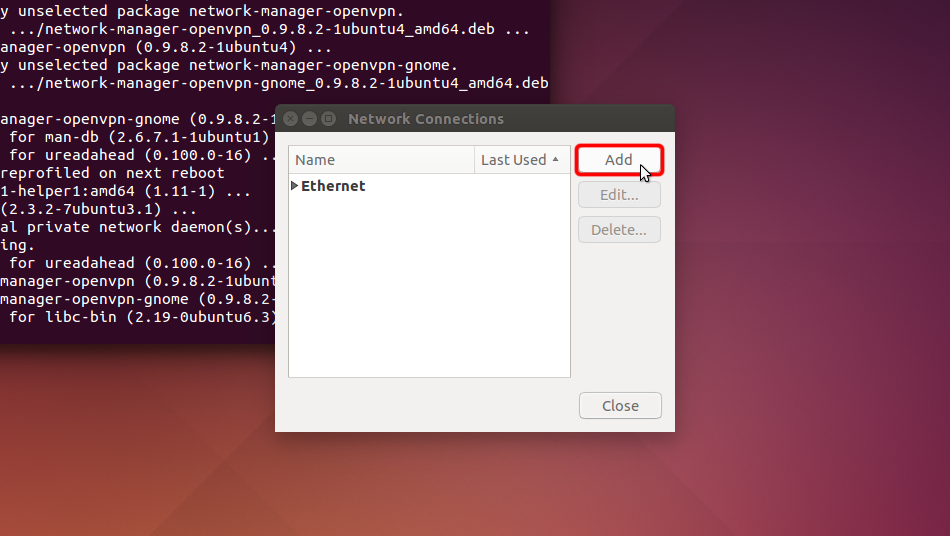
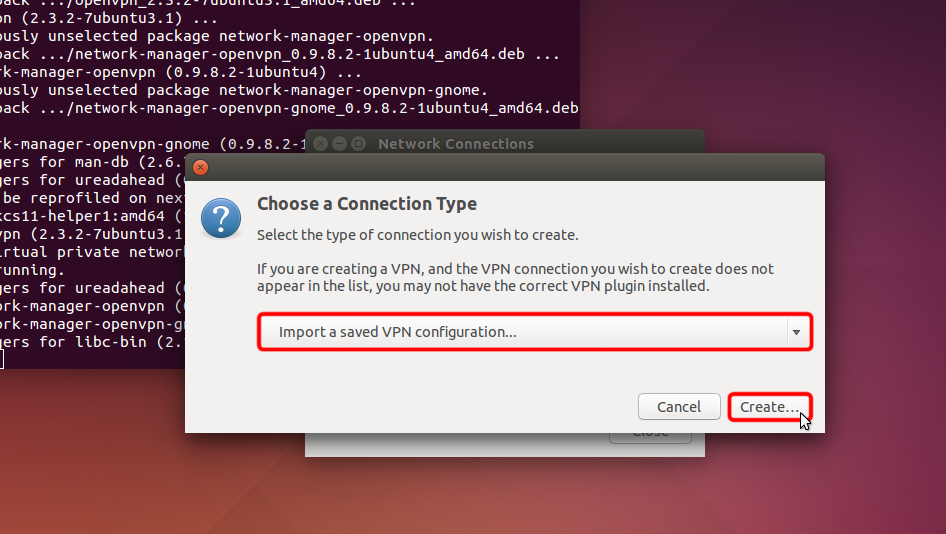
Klicken Sie auf "Hinzufügen".
Klicken Sie auf "Gespeicherte VPN-Konfiguration importieren..." und klicken Sie auf "Erstellen"
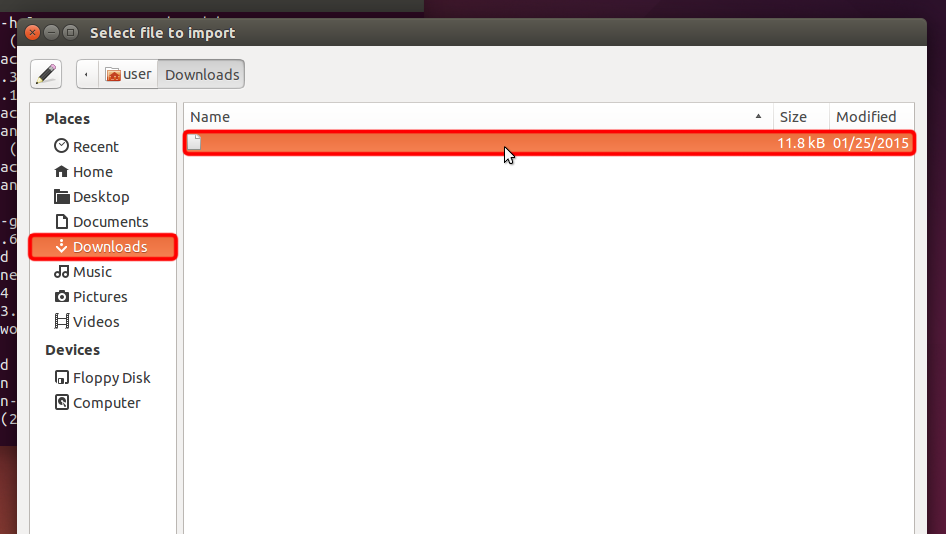
Laden Sie die OpenVPN-Konfigurationsdatei (.ovpn-Datei) herunter, wählen Sie den Abschnitt "Downloads" und öffnen Sie die Datei Trust.Zone-VPN.ovpn , indem Sie darauf doppelklicken.
OpenVPN (.ovpn) Datei: VERSTECKTE. Melden Sie sich an oder loggen Sie sich ein, um zu sehen.
 Trust.Zone-VPN.ovpn
Trust.Zone-VPN.ovpn
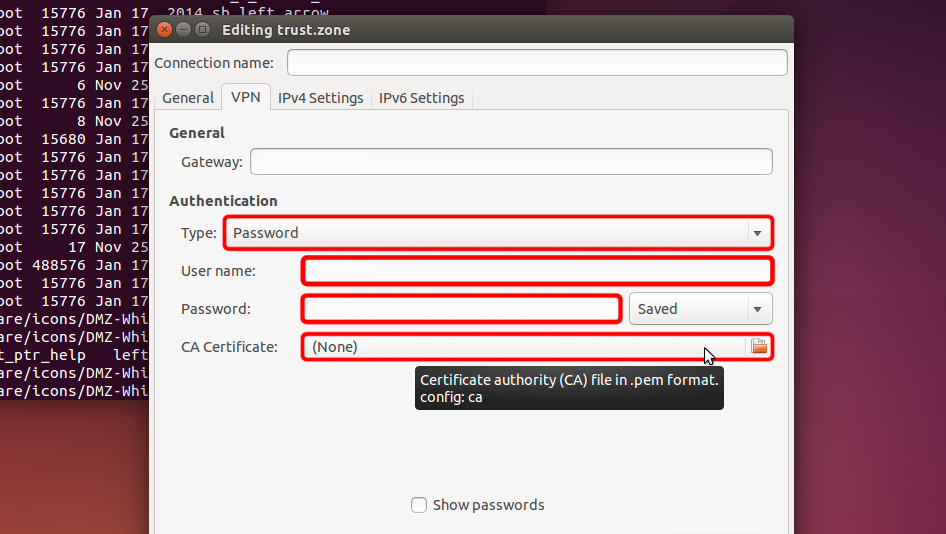
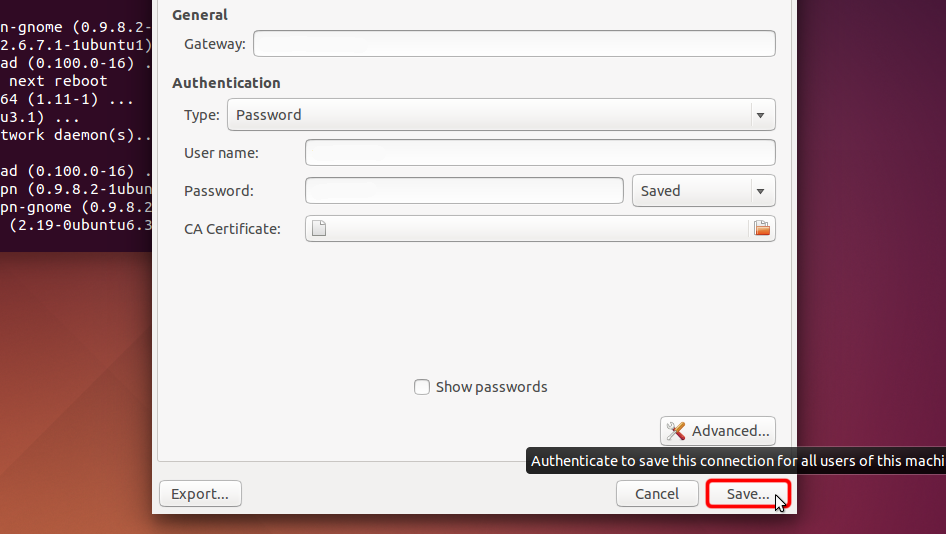
Wählen Sie "Passwort" aus dem Dropdown-Menü "Typ" und geben Sie Ihren VPN-Benutzernamen und Ihr Passwort ein.
Your VPN Username: VERSTECKTE. Melden Sie sich an oder loggen Sie sich ein, um zu sehen.
Your VPN Password: VERSTECKTE. Melden Sie sich an oder loggen Sie sich ein, um zu sehen.
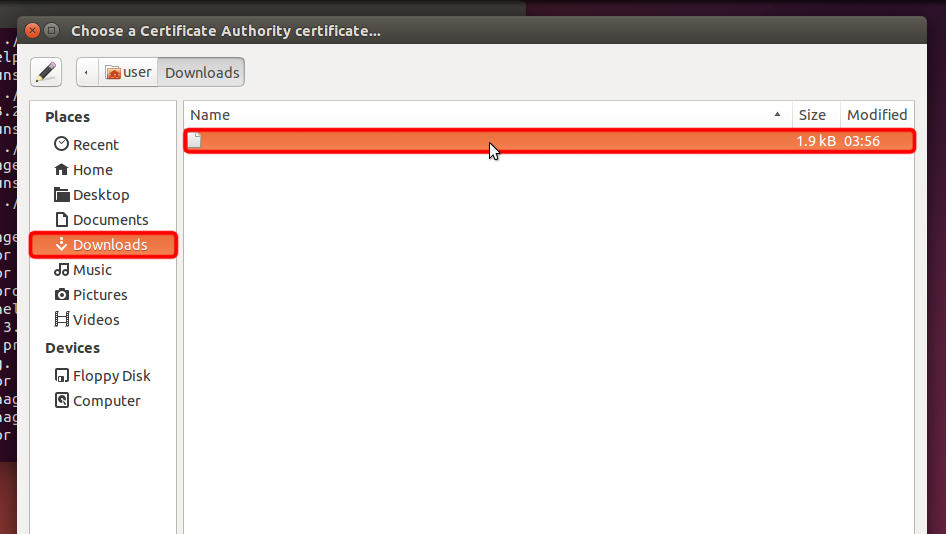
Laden Sie die Zertifikatsdatei herunter und klicken Sie auf die Dateiauswahl "CA-Zertifikat", um die Zertifikatsdatei auszuwählen.
Certificate file: VERSTECKTE. Melden Sie sich an oder loggen Sie sich ein, um zu sehen.
 Trust.Zone-VPN
vpn.trust.zone
Trust.Zone-VPN
vpn.trust.zone
Navigieren Sie zu "Downloads" und doppelklicken Sie auf den Namen des Zertifikats, um ihn auszuwählen.
 Trust.Zone-VPN.pem
Trust.Zone-VPN.pem
Klicken Sie auf "Speichern..." , um die VPN-Verbindungseinstellungen zu speichern.
 vpn.trust.zone
Trust.Zone-VPN.pem
vpn.trust.zone
Trust.Zone-VPN.pem
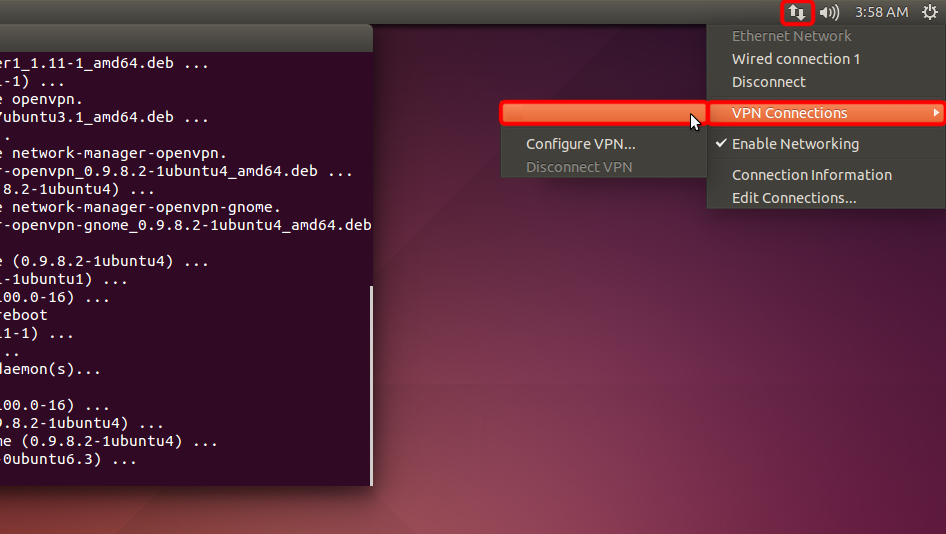
Klicken Sie auf das Netzwerkmenüsymbol, wählen Sie "VPN-Verbindungen" und klicken Sie auf den Namen der von Ihnen erstellten Verbindung, um eine VPN-Verbindung herzustellen.
 Trust.Zone-VPN
Trust.Zone-VPN
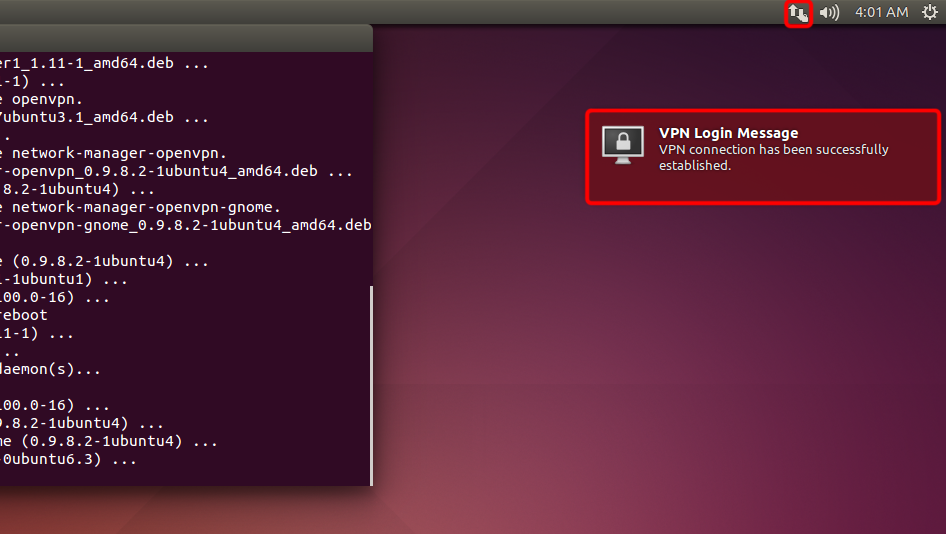
Wenn die Verbindung erfolgreich hergestellt wurde, wird der Status in der Menüleiste und in der Sprechblase angezeigt.
Um Ihre VPN-Verbindungen zu verwalten, klicken Sie auf das Symbol "Netzwerkverbindungen", wählen Sie "VPN-Verbindungen" = > "VPN konfigurieren...".
Nachdem Sie sich mit dem Trust.Zone VPN verbunden haben, ändert sich Ihre IPv4-IP-Adresse, aber Ihre IPv6-Adresse bleibt unverändert.
Dies ist kein Problem, falls Ihr ISP IPv6 NICHT unterstützt, aber falls dies der Fall ist, kann Ihre IPv6-Adresse durchsickern.
Der beste Weg, um zu verhindern, dass IPv6 durchsickert, empfehlen wir, IPv6 in Ihrer Linux-Distribution zu deaktivieren. Hier erfahren Sie, wie Sie das tun können.
Um zu überprüfen, ob IPv6 bereits deaktiviert ist, führen Sie bitte den folgenden Befehl aus:
cat /proc/sys/net/ipv6/conf/all/disable_ipv6
Wenn der Befehl 1 zurückgibt, ist IPv6 bereits deaktiviert und Sie können die folgenden Schritte überspringen. Falls der Rückgabewert 0 ist, befolgen Sie bitte die folgenden Anweisungen:
Bitte öffnen Sie die Datei /etc/sysctl.conf in Ihrem bevorzugten Texteditor. In unserem Beispiel verwenden wir den Nano-Editor.
sudo nano /etc/sysctl.conf
Fügen Sie am Ende der Datei die folgenden Zeilen hinzu:
net.ipv6.conf.all.disable_ipv6 = 1
net.ipv6.conf.default.disable_ipv6 = 1
net.ipv6.conf.lo.disable_ipv6 = 1
Nun können Sie die Datei speichern und den Editor beenden. Falls Sie nano verwenden, müssen Sie Strg-O drücken, um Änderungen zu schreiben, und Enter drücken, um das Schreiben der Datei zu bestätigen. Dann können Sie Strg-X drücken, um den Editor zu verlassen.
Führen Sie den folgenden Befehl aus, um die Kernel-Parameter zu aktualisieren:
sudo sysctl -p
Der Befehl gibt Zeilen zurück, die Sie zu /etc/sysctl.conf hinzugefügt haben
Wenn Sie nun cat /proc/sys/net/ipv6/conf/all/disable_ipv6 ausführen, sollte der Befehl 1 zurückgeben. Das bedeutet, dass IPv6 deaktiviert ist, so dass ein IPv6-Leck nicht mehr möglich ist.
Öffnen Sie die Trust.Zone Hauptseite ooder laden Sie sie neu, wenn sie bereits geöffnet ist, um zu überprüfen, ob Ihre Verbindung mit Trust.Zone VPN korrekt hergestellt wurde.
Sie können auch unsere Verbindungsprüfungsseite besuchen.
 Deine IP: x.x.x.x ·
Deine IP: x.x.x.x ·  Norwegen ·
Sie sind jetzt in TRUST.ZONE! Ihr wirklicher Standort ist versteckt!
Norwegen ·
Sie sind jetzt in TRUST.ZONE! Ihr wirklicher Standort ist versteckt!