<< Alle Beiträge17 Oktober 2024
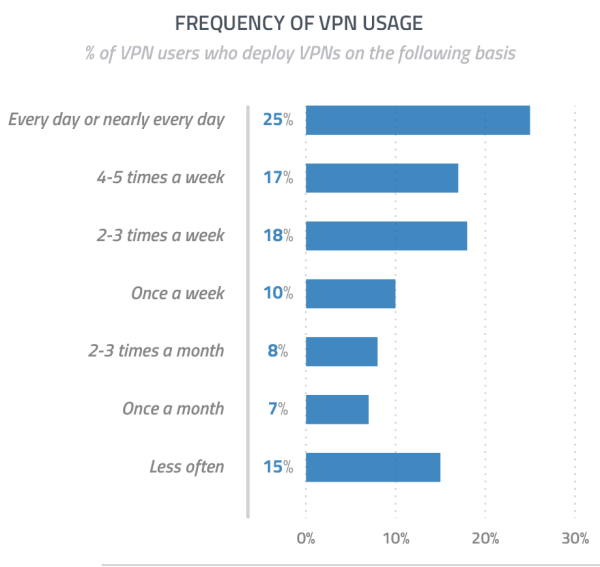
1 in 4 VPN users accessing daily – according to new report by GlobalWebIndex. The main question of the survey was “How frequently do you use VPNs to connect the Internet?
At least, 10% of VPN users access VPN once a week. 7% - once a month. Report was presented by GlobalWebIndex Web Analytics Company. weiterlesen...
20 September 2024
International human right organizations have been expressing concern about how Russian authorities have been repressing free press for years. Instead of improving, the situation has gotten worse and worse until censorship involved the Internet as well.
With the Ukraine invasion, furthermore, censorship in Russia has reached levels never seen before: Russian citizens can’t access thousands of websites and new ones are being obscured every month.
According to the latest report, VPN usage in Russia increased by 900%
When it comes to online restrictions, however, there is a way of getting around them, and in this article, we’re exploring how. weiterlesen...
18 August 2024
In certain regions, accessing X (formerly known as Twitter) can be challenging due to government-imposed restrictions. Trusted VPN services offer a reliable solution to bypass these blocks, enabling you to connect to X securely and privately.
Here’s a detailed guide on how to use TrustZone VPN to unblock X. weiterlesen...
2 August 2024
In recent times, access to Instagram has been restricted in Turkey, causing frustration among many users who rely on the platform for communication, entertainment, and business. Turkey has blocked Instagram as part of broader internet censorship measures following specific events and due to ongoing regulatory and political pressures.
The legal amendments to Turkey's internet laws have compelled social media companies to comply with government demands, under threat of severe penalties, including service throttling or outright bans. This regulatory environment has led to increased censorship and has put pressure on platforms like Instagram, Facebook and Twitter to conform to these regulations to avoid disruptions.
For users in Turkey who want to unblock Instagram, using a VPN like Trust.Zone can be an effective solution. Here’s a step-by-step guide weiterlesen...
30 Juli 2024
The Olympic Games are an event watched by millions around the world. However, due to regional broadcasting restrictions, some viewers might face difficulties accessing their preferred coverage. A Virtual Private Network (VPN) is a powerful tool that can help bypass these restrictions, providing a seamless viewing experience.
Here’s a comprehensive guide on how to watch the Olympic Games 2024 in Paris using a free VPN. weiterlesen...
16 Juli 2024
Our vacations are not just about relaxing on a beach or exploring new cities. Yhey also involve staying connected.
Whether it’s sharing photos on social media, checking emails, or accessing online banking, we rely heavily on the internet even when we are away from home. This connectivity, however, comes with its own set of risks.
Here’s why using a VPN (Virtual Private Network) when you travel is essential for a secure and seamless vacation experience. weiterlesen...
8 Juli 2024
Several world's leading VPN comparison services have rated Trust.Zone recently.
See the highlights of Trust Zone VPN reviews here weiterlesen...
1 Juli 2024
Did you know that Trust.Zone support the latest Military-Grade Encryption algorithm - AES-256 encryption?
AES256 is a symmetrical encryption algorithm. It is otherwise known as “military-grade encryption” because it is adopted by the U.S. and Canadian governments as standards for encrypting transited data and data at rest. Because of the 256-Bits length of the key and the number of hashes (14), it takes a long time for a hacker to perform a dictionary attack weiterlesen...
18 Juni 2024
You’ve no doubt heard the term VPN before. This is hardly surprising; consumers and businesses are becoming increasingly aware of how important their privacy is and the need to protect their data. This awareness has, in part, grown due to the rise in cyber-attacks and data breaches in recent years.
What’s more, cybercrime is expected to increase in the coming years, with its cost estimated to reach 17.65 trillion US dollars in 2025.
For this reason, many turn to security tools such as VPNs to protect themselves from cybercrime. This article will take you through what a VPN is, how it works, and how exactly it helps with data protection. weiterlesen...
6 Juni 2024
Internet scams are ever-prevalent threats online. As technology evolves, cybercriminals get more sophisticated with their malicious methods. You could lose your entire life savings and even your identity when you fall victim to their attacks.
What can you do? Enter AI (artificial intelligence) into the picture. AI technology has been advancing in recent years and is getting more popular by the day.
In this post, we explore how AI is disrupting traditional VPN-based scams. How does it prevent online fraud? weiterlesen...