<< Alle Beiträge13 Januar 2023
Every person or business using the internet will be aware of the danger of cybersecurity threats. We know we can protect ourselves by using different passwords and avoiding suspicious downloads. But cyber attackers are beginning to create more sophisticated ways of exploiting vulnerabilities.
One of the most dangerous threats at the moment is clickjacking. Think about how often you use websites without considering what you’re clicking. While this usually isn’t anything to worry about, clickjacking has created a new threat.
Clickjacking works by placing a malicious set of links over an innocuous-looking website. This means that victims enter passwords or click links that they think are legitimate parts of the original website but are in fact on an invisible page.
This guide will show how you can recognize clickjacking attacks and keep your personal details or business secure. In today’s digital world, protecting yourself from cyber threats has never been more critical, and preventing clickjacking is a crucial part of this. weiterlesen...
9 Januar 2023
Streaming is addictive, and sometimes we tend to ignore the drawbacks of the things with which we become addicted, and that’s where the problem arises. The streaming industry is rising but along with some severe malware threats and cyberattacks.
Therefore, we have come up with seven tips to get your streaming system to prepare for any kind of malware and cyberattack. weiterlesen...
8 Januar 2023
Cybersecurity mistakes either happen unintentionally or due to a lack of taking proper action, thus causing a security issue like a data breach. An example of an activity that might cause these errors is compromising your IP address.
Other reasons include clicking an unsafe link, missing updates, and misconfiguration. Businesses and individuals have suffered massive losses and problems due to cybersecurity issues like system disruption and data breaches.
One example of how disruptive these errors can be is a system that has been affected by ransomware. The malware encrypts the files to a point where the original owner can't access their information. weiterlesen...
23 Dezember 2022
Some business owners skip out on cybersecurity because they think it is expensive, unimportant, and complicated. However, nowadays, cybersecurity is a valuable investment.
Cybersecurity threats are consistently increasing and becoming more sophisticated. These threats can affect companies of any size or industry and cost them millions. Fortunately, there are various ways to mitigate the risks of cyberattacks. Here are some of the proven ways: weiterlesen...
1 Dezember 2022
A common belief is that Mac devices are more secure than their Windows or Linux counterparts, and it isn’t entirely misplaced. Privacy advocates cite Apple’s full control over the hardware and software used in their devices and the fact that Mac owners are fewer in number than Windows are some of the reasons for this sense of security.
But strong security doesn’t always imply immunity. Over the years, cybersecurity experts have sounded alarms on exploits within Mac devices like the 2019 Gatekeeper exploit. Although no major instances of hackers using this exploit have been reported, waiting for one to happen is ill-advised for obvious reasons.
Complacency is a worse adversary than hackers themselves. It’s important to always think that hackers will find a way into your device, Mac or otherwise. Consider the following things worth knowing about security for Mac devices. weiterlesen...
30 November 2022
Cyber threats change frequently. Therefore, it’s essential to keep your cybersecurity measures up to date. Additionally, educating your staff on cybersecurity awareness is also vital. As a result, you can reduce your business’s vulnerability to cyber threats.
Here is a list of steps to protect your business from cyber threats. weiterlesen...
26 November 2022
Cybercrime has become an increasingly significant problem in the 21st century. Businesses and individuals risk hacks, scams, or someone stealing their personal information. With hackers developing more advanced techniques of breaching security walls, more robust cybersecurity measures in place have never been more critical.
Fortunately, cybersecurity stakeholders have taken tremendous steps in recent years to combat these threats. From offering cybersecurity training to investing in cutting-edge security technologies, you and your business can stay ahead of the curve.
As the new year approaches, new cybersecurity trends will dominate the conversation. Here’s a list of the cybersecurity trends to watch out for in the coming year and possibly beyond: weiterlesen...
17 November 2022
As the workplace becomes more digital, your employees should have appropriate skills to be safe when surfing the internet. Your employees should know the risks and steps to take to protect themselves from cyber-attacks.
To be secure online, you must constantly educate your staff and make changes following technological advancements. Also, you may consider the help of a company with IT support services to clean up your computer network, eliminate potential problems, and help your team implement efficient technology. Having said that, the following are some internet safety tips you can implement in the workplace: weiterlesen...
9 November 2022
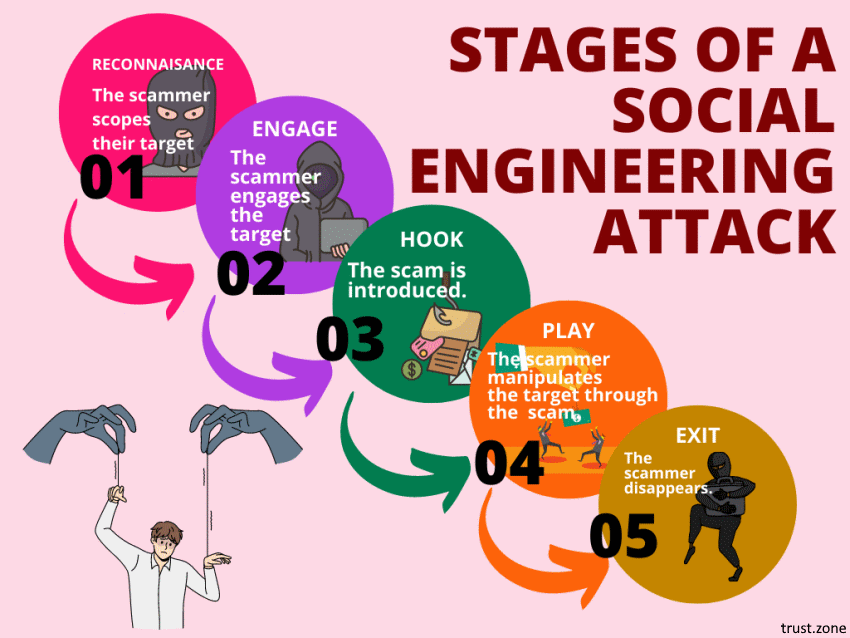
Social engineering attacks are on the rise. In fact, they’re among the most successful and insidious types of cybercrime active today.
Worst of all, you can’t protect yourself from all social engineering attacks by just boosting your computer security. A good social engineering attack doesn’t target your software. Instead, it targets the human element. It tries to trick you, often by playing on your emotions. Social engineering attackers are scammers who use human emotions as the tools of their trade.
To protect yourself from social engineering attacks, you need to secure your mindset as well as your technology. Let us show you how. weiterlesen...
5 September 2022
Before you do anything online, familiarize yourselves with your opponents.
Returning to the ‘brick through the window’ analogy, part of the preparation for a break-in is knowing the criminals' tactics. If you know a thief is going to use a brick to break in, add double glazing.
Similarly, if your business is to stay safe online, you need to know the common practices of hackers. This is where this article comes in handy. We’ll focus on three of these tactics: phishing, vishing, and smishing (we promise we didn’t make those words up). weiterlesen...