<< Alle Beiträge18 Januar 2024
Hackers don’t limit their attacks to e-commerce sites. Blogs are vulnerable as well. WordPress and other suites are so popular that cybercriminals make it their business to learn how to exploit any weaknesses.
When they find those openings, they might take your site hostage, redirect your visitors to nefarious websites, or retrieve sensitive data about your business or customers.
In any case, it’s imperative that you ensure your blog is locked down. You can start this process by checking out the following security tips. weiterlesen...
8 Januar 2023
Cybersecurity mistakes either happen unintentionally or due to a lack of taking proper action, thus causing a security issue like a data breach. An example of an activity that might cause these errors is compromising your IP address.
Other reasons include clicking an unsafe link, missing updates, and misconfiguration. Businesses and individuals have suffered massive losses and problems due to cybersecurity issues like system disruption and data breaches.
One example of how disruptive these errors can be is a system that has been affected by ransomware. The malware encrypts the files to a point where the original owner can't access their information. weiterlesen...
19 Dezember 2022
Criminals around the world pose serious risks to the property and lives of any business. Therefore, investing in the sturdiest business security systems is crucial. These tools can help ensure your company is safe from malicious intrusions.
If you’re concerned that the security weaknesses in your current system are growing, it’s best to conduct a careful assessment. After all, as technology advances, criminals and burglars are also innovating their techniques and methods.
Check out the following signs to determine if your security system needs an upgrade. weiterlesen...
1 Dezember 2022
Today’s businesses are more reliant on technology than ever before. The network is the backbone of this technology, and keeping it running smoothly is critical so your business functions correctly. However, networks aren’t perfect and can fail from time to time. When this happens, it can be costly and disruptive to your business.
That’s why developing strategies in place is critical in enhancing network reliability and efficiency. By improving these two areas, you can minimize the impact of network disruptions and keep your business operations running efficiently.
Here are some top strategies to enhance network reliability and efficiency: weiterlesen...
30 November 2022
Reducing your digital footprint is an essential part of staying safe online. If you take measures to control what information about you is available online, you can help protect yourself from identity theft, fraud, and other cyber crimes.
So choose your privacy settings wisely, use incognito mode while browsing, and be thoughtful about what personal information you share online. Also, don’t forget to unsubscribe from unwanted emails. Use security tools, too.
Following these simple tips will go a long way towards keeping your personal information safe and secure. weiterlesen...
9 November 2022
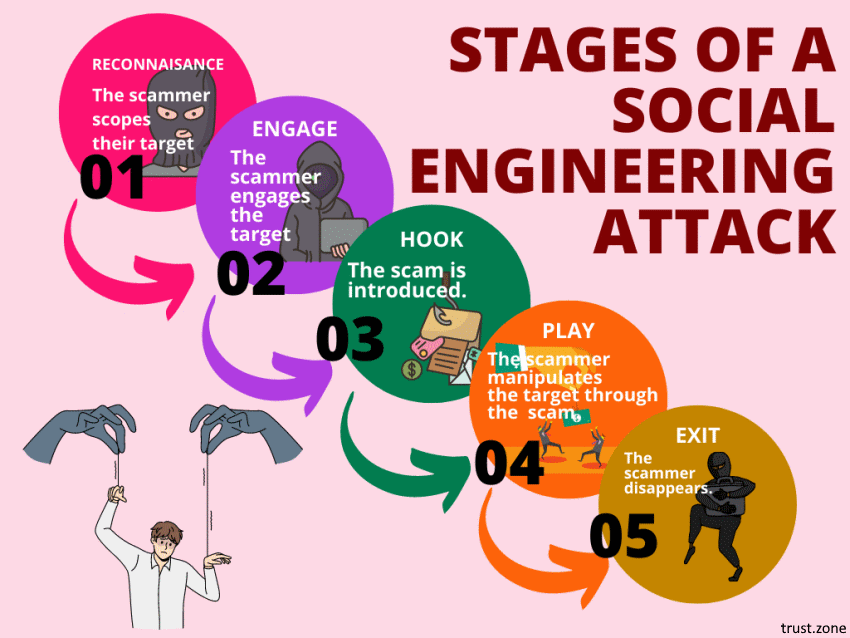
Social engineering attacks are on the rise. In fact, they’re among the most successful and insidious types of cybercrime active today.
Worst of all, you can’t protect yourself from all social engineering attacks by just boosting your computer security. A good social engineering attack doesn’t target your software. Instead, it targets the human element. It tries to trick you, often by playing on your emotions. Social engineering attackers are scammers who use human emotions as the tools of their trade.
To protect yourself from social engineering attacks, you need to secure your mindset as well as your technology. Let us show you how. weiterlesen...
24 August 2022
With so much technology these days, it’s hard for companies and organizations to go without it. Since technology is now the lifeblood of a company, it’s important to keep that blood flowing.
However, cybercriminals are also getting savvy with technology. They’ll launch cyber-attacks on an unsuspecting business and wreak havoc on systems and assets.
Has this ever happened to your company? Or have you feared this for your company? You’re not alone. In just 2021 alone, there were 80,000 cyber-attacks per day – that’s over 30 million attacks annually
Don’t let this happen to your company. Below you will learn of the 6 common mistakes in cybersecurity, and how you can avoid them at all costs: weiterlesen...
18 Mai 2022
With cybercrime on the rise in recent years, companies are facing more cybersecurity issues than ever before.
As newer technologies take even more operations online, businesses are facing an increasing cybersecurity risk.
Where they used to be able to control their own networks and audit their own devices, many are now spread out over great distances and reliant on their employees’ password strength to keep their information secure. weiterlesen...
8 Februar 2022
The importance of cybersecurity in today's business climate has become essential. Its importance in the environment of business cannot be overstated.
Following through on cybersecurity trends is vital for organizations and companies for many reasons.
A cybersecurity policy is a written document that explains the technical and procedural guidelines for employees to ensure effective protection from cybersecurity threats and ransomware attacks. This policy primarily contains information about establishments or companies' security procedures, digital safeguards, and operational countermeasures in the case of a cyber security threat. weiterlesen...
12 Januar 2022
For anyone who uses the internet, cyber attacks remain a big concern.
Cyber attackers are getting smarter. They always have a trick or two to breach the most secure systems.
Technologies like internet banking, online payments, cloud computing, and crypto exchanges are great. That said, there is an element of vulnerability about them. It forces users and organizations to take protective measures to avoid any disaster. So, as the cyber world continues to advance, what trends can we expect in 2022?
In this post, we will talk about the most dominant cyber security trends in 2022. So you can stay well-prepared to counter any security threats. weiterlesen...